How to Recover from a Ransomware Attack
There’s always a chance you could fall victim to a ransomware attack. We’ll walk you through the response and ransomware recovery process.
Table of Content
Best case scenario, your business avoids becoming a ransomware victim through robust prevention and detection methods.
But – it’s important to remember that ransomware is always evolving.
RansomOps are becoming increasingly sophisticated. Cybercriminals now use AI-driven tools, new extortion techniques, and take advantage of new opportunities offered by RaaS. So, despite your best efforts, there’s always the chance that bad actors will eventually end up in your system.
In this article, we’ll walk you through the response and recovery process – one step at a time.
Look, it’s not necessarily the end of the world if some malware slips through the cracks and infects your system. You just need to be prepared.
Your immediate goal is containing the threat, protecting stakeholders, and getting things up and running ASAP to minimize damage and disruption. Employees should be prepared to follow the documented incident response plan – first checking to see if backups have been impacted and whether it’s possible to contain and mitigate the threat right away.
Now, if immediate mitigation isn’t a possibility you’ll need to work through a few more steps. Here’s a quick rundown of the ones outlined in the CISA framework:
If your company has been hit by ransomware attack, employees should immediately notify senior management and the legal department of the attack.
Getting an attorney involved from the get-go is important as it ensures the investigation is protected by attorney-client privilege and can help orgs reduce the risk of getting hit with regulatory fines or class action lawsuits.
According to MIT, federal agencies may be able to help you recover lost data. In some cases, they may be able to trace attacks to a variant that has been decrypted – allowing you to avoid payment and recover your data – or recover ransom funds (though in some cases like Colonial Pipeline, some funds may be lost due to Bitcoin’s inherent volatility).
Determine which systems, accounts, files, emails, etc. were infected
Isolate and contain any files, software, devices directly impacted by the attack, as well as anything that may be connected to those infected systems – remote desktops, VPNs, other cloud-based assets, etc.
Isolate and contain any files, software, devices directly impacted by the attack, as well as anything that may be connected to those infected systems – remote desktops, VPNs, other cloud-based assets, etc.
Some strains of ransomware can compromise system stability. In these cases, avoid updates and reboots until ransomware has been successfully removed – otherwise, your files could remain locked in an unrecoverable state.
Check out the No More Ransom Project website to find out more about the strain, the attacker, and, potentially, gain access to a free decryption key.
Check all security analytics tools, logs, etc. for evidence of a compromise such as precursor malware, unusual activity, or trigger files across the entire network. You’ll also want to see if you can determine the attack style and/or find out more about how this particular strain behaves and spreads.
Collect logs and evidence and take a system memory capture of any devices impacted by the incident, taking extra care to preserve evidence for deeper analysis and investigation.
Keep in mind, you’ll want to capture as much evidence as you can before moving forward with the ransomware recovery process to aid law enforcement, cyber insurers, and external security experts in their investigation.
Next, you’ll want to disconnect any infected backups and at-risk systems. Attackers typically go after backup systems because they know victims will immediately try to recover critical documents and data so they can avoid paying the ransom or succumbing to additional extortion threats.
You’ll also want to avoid connecting backups to infected systems or devices and quarantine any backups that may be compromised – otherwise, you’re just helping the threat actor make quick work of your network.
While it makes sense that companies tend to focus their ransomware strategy on prevention and detection, reestablishing continuity should be a top priority. Bring systems back online as soon as possible.
Test any systems you suspect have been infected before bringing them back online. Document procedures used to resolve issues.
Determining whether or not to pay the ransom is a difficult decision. In some cases, payment may be the fastest, most cost effective path to recovery. However, there’s no guarantee that making the payment will result in the safe return of your data and it may make you more susceptible to future attacks.
Whether paying the ransom is the right decision depends on several factors – it’s generally frowned upon (FBI, experts say it encourages ransomware attackers to continue this behavior).
You’ll want to perform a quick cost-benefit analysis based on the scenario, potential outcomes, and from there, make a decision with harm reduction in mind.
Additionally, HBR recommends that orgs ask themselves the following questions when making this call:
Note that your initial “response” is different from your long-term “recovery.” At this stage in the game, you’re trying to triage the situation so you get up and running again – and buy yourself some time to explore permanent solutions.
Once a system is identified as “infected,” it needs to be removed from the network and quarantined – away from cloud environments, apps, services, wifi, etc.
Failing to isolate ASAP can lead to more damage, as ransomware will continue to spread through the digital estate and encrypt more files. According to an IBM white paper, you’ll want to run endpoint detection and response (EDR) immediately following the attack. This will help you isolate infected systems and keep them online, allowing you to retain critical evidence and data, without causing further harm to the system.
If you don’t have an EDR solution, you may have to terminate access to the network. It’s a last resort that can lead to data loss, but it minimizes potential damage to other parts of the network.
The eradication phase focuses on removing ransomware from infected systems. In some cases, the process is relatively short, whereas in others, removing ransomware is a complex, lengthy process. It all depends on the scope of the attack and how much damage was done.
Some ransomware variants can make infected systems unstable – so you’ll want to avoid reboots or updates and keep systems online until you’ve successfully removed the malware.
After you’ve completed the containment and eradication process, your next move is to work through the following steps to restore your system:
After experiencing a ransomware attack – particularly one involving a systemic identity compromise – you’ll want to go ahead and assume all communication channels have been infected.
Before taking any additional action, you’ll want to make sure that your team can communicate securely – allowing you to proceed with your investigation and ransomware recovery process without the threat actor’s knowledge.
Most ransomware attacks are identity-based, so you’ll want to make sure that your post-attack ransomware recovery process focuses on strengthening identity and access management protections.
If you haven’t already, implement multi-factor authentication (MFA), single sign-on, and update access permissions, and simplify identity management and governance.
Solutions like Azure AD allow you to configure conditional access policies based on contextual factors like device, user, and real-time risk intelligence, and automate policy governance and provisioning.
You can even run reports that identify “risky users,” events, and log-in attempts and take immediate action against suspicious activity.
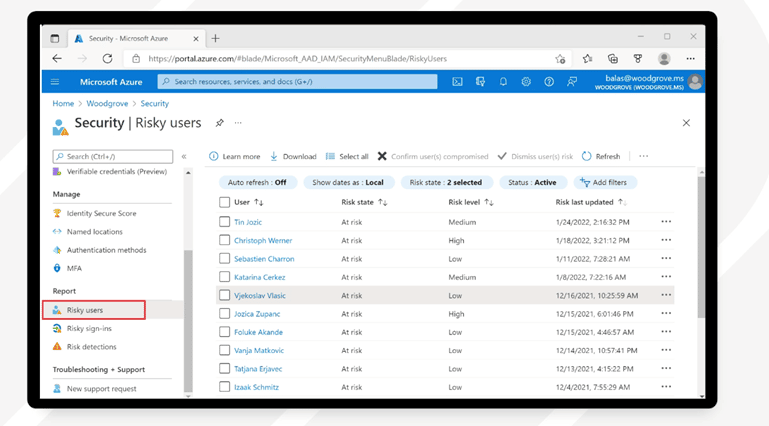
Microsoft’s Detection and Response Team (DART) recommends updating all apps and services post-breach and implementing an inventory and asset solution such as Endpoint Configuration Manager so that you can manage all updates, patches, and installs from one place moving forward.
Use offline backup files to restore data and reconnect to the system, taking extra precautions to avoid reinfection. It’s a good idea to perform this task in a sandbox environment to minimize your risk. Additionally, you’ll want to make sure that you verify the status of your backups at the time of recovery.
In the IBM paper mentioned above, experts warn that there’s a chance that attackers have been hanging out in your system for months, encrypting backups. Or – they may lie dormant for even longer, planting persistence mechanisms into backups. Make sure you store backups in a separate location and check them regularly – ensuring that they haven’t been tampered with.
You’ll also want to avoid making policy exceptions for specific users or business units that make it possible to avoid patching vulnerabilities.
In the short-term, DART advises orgs to isolate vulnerable apps and devices to avoid getting hit by a follow-up attack. Though, long-term, security experts recommend adapting your acquisitions process so that you only work with vendors that provide adequate protections.
Microsoft experts recommend investigating the compromised environment – after ensuring that you can communicate and collaborate securely.
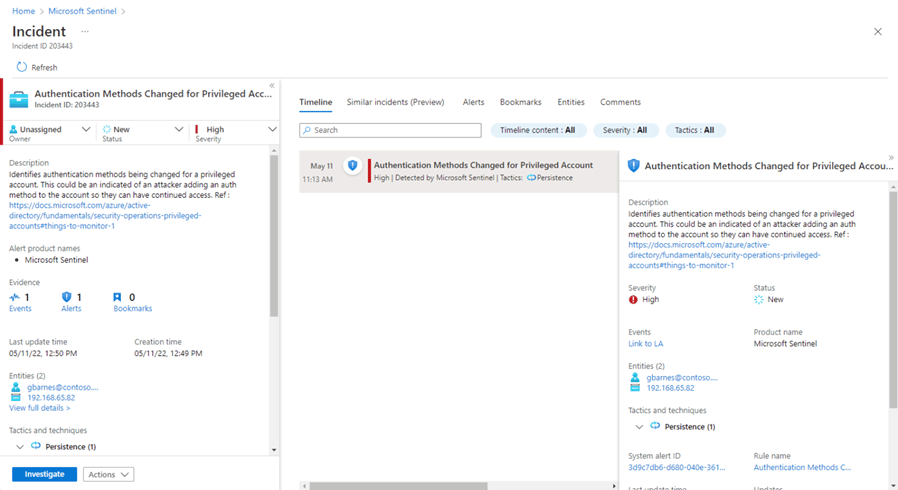
Sentinel comes with deep investigation tools to help users understand the scope of the attack and identify the root cause behind the incident.
The built-in dashboard allows you to search for incidents – filtering by severity, compromised entities, trigger events, or other factors. You can review a timeline of the incident to learn how the attack went down. Or, review similar incidents to learn more about the attack in a broader context.
Advanced threat hunting – process that involves proactively searching for the presence of threat actors, malware, etc. within the digital environment.
Yeah, you do need to talk about what happened – it’s the first step toward making changes so that this won’t happen again. Document lessons learned from the incident and use them to refine your ransomware policies and procedures so you’re better prepared for future attacks.
The last step in your post-incident ransomware recovery process is making sure you can respond quickly and confidently to future attacks.
Or better yet, avoid them in the first place. If you haven’t already, implement a Zero Trust policy.
According to Microsoft experts, recovering from a cyber incident means forcing security changes that should have been implemented a long time ago. Often, what should have been a years-long process of incremental updates must happen within a matter of weeks.
This process also involves significant behavioral and operational changes – which, of course, tend to be the hardest changes any organization will have to make. Things like how to administrate the environment, deploy machines, or monitor identities, activity, and data.
For example, you might look for a detection and response platform to help with monitoring and preventing issues. But, if you’re already using the latest and greatest tools, you’ll need to focus on training your teams, making sure they’re using tools properly, that they understand how to interpret data, etc.
Finally, document the new game plan, communicate changes to your team, and make sure tgat leadership supports and enforces it.
Recovering from a ransomware attack is a multi-step process that requires a lot of planning and preparation, as well as the right set of tools.
Velosio is a certified Microsoft partner with over 30 years of experience helping clients get the most from their digital investments. While we’re not a security company, Velosio experts understand the ins and outs of the Microsoft ecosystem and are prepared to help you find and implement the solutions that maximize business value and help you stay safe in the cloud.
Contact us today to learn more about how we can help you prevent, detect, and recover from ransomware attacks.
Campfire365 Ep.1 - The Big Disaster: Is Your Organization Ready for the Next Major Catastrophe