Elements of a World-Class Ransomware Strategy
Building a world-class ransomware strategy calls for a modern approach to cybersecurity — built on the principles of Zero Trust.
Table of Content
Historically, IT resources existed within clear boundaries. You’d have all servers, devices, and software in one place, protected by perimeter-based solutions.
Often, identity and access controls existed in this binary where the decision to “allow” or “deny” requests was based on absolutes. For example, internal traffic is inherently trustworthy, while external traffic is a threat — without considering the contextual factors that determine what risk that user poses to the business.
Now, that sort of black-and-white approach has always had issues. But, legacy cybersecurity strategies have become, well, much more problematic in the last few years due to digital transformation.
Today, everything is both hyper-connected and extremely spread out. The perimeter no longer exists. Nor does the concept of inherent trust. There’s big data, remote work, and the IoT, among other things — adding even more complexity to the mix, and a huge influx of vulnerabilities for threat actors to exploit.
The point is, building a world-class ransomware strategy calls for a modern approach to cybersecurity — built on the principles of Zero Trust. In these next few sections, we’ll explain what that means in more practical terms.
Zero Trust is a set of policies based on the underlying principle, “never trust, always verify.”
It’s flexible, adaptable, and fast-moving.
In other words, ideal for securing a world in which rapid and unrelenting digital transformation is an ongoing reality.
Now, it’s important to understand that Zero Trust doesn’t represent a specific strategy, solution, or technology. Rather, it’s a framework for establishing trust between resources and users in real-time, as needed — and continuously revalidating those connections.
As Deloitte experts explain in the firm’s 2021 Future of Cyber report, Zero Trust is designed to work for all organizations – regardless of size, sector, budget, or business goals – but it’s absolutely not a one-size-fits-all framework.
That means, it’s not enough to follow general best practices — those best practices must be tailored to meet your org’s unique set of needs and align with your actual business goals.
Done right, Zero Trust provides the assurance that you’ve covered all of your bases – so that unexpected threats and vulnerabilities won’t catch you by surprise later on.
The framework is designed in such a way that ransomware protections are added to your estate one layer at a time – until each of the following “security pillars” have been accounted for:
We’ve covered these pillars in a previous post on anti-ransomware tool guidance, and you can also find them throughout the Microsoft Security content, downloads, and documentation.
That said, if you’re coming at this with Zero Trust experience to speak of, you might want to look into the Microsoft RaMP initiative – which offers technical deployment guidance across a handful of high-priority areas:
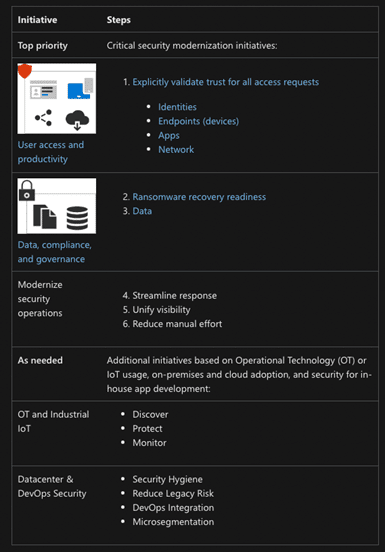
While the RaMP initiative does address all elements of the Zero Trust architecture, the idea is to help organizations focus on high-impact areas first. So, you’re starting with identities and endpoints – because they represent the biggest threat to your business, then working your way through apps, networks, and beyond.
Integration is central to all digital strategies — and ransomware is no exception. Zero Trust hinges on establishing unity and integration across the entire digital estate — offering the end-to-end visibility, actionable insights, and agility needed to defend against ransomware.
Beyond making sure that your estate is fully-protected and 100% free of gaps and silos that can get you in trouble, you’ll want to avoid leaning on too many solutions. And, instead, aim to invest in interoperable tools that cover multiple pillars.
Fragmented security solutions can result in coverage gaps and unnecessary complexity – creating extra work for IT and introducing new risks to your system. It’s harder to detect incidents as they’re happening, let alone mount a proactive defense against future threats based on suspicious patterns and anomalies flagged by your system’s AI.
Alternatively, if companies implement security measures that add friction to daily workflows, employees will find workarounds in the form of unsanctioned apps (aka shadow IT).
Either way, orgs are essentially serving valuable documents and data to attackers simply by making things harder than they should be.
These factors – among others – are the key reason why we put so much emphasis on the “Microsoft ecosystem.” These solutions are designed to work together, as a single ransomware-fighting unit.
Business leaders pick and choose the capabilities they need to protect their entire estate – whether you need to protect remote teams, IoT and OT networks, or complex hybrid set-ups that span on-prem servers and cloud-based services.
Strong governance is directly connected to the success of your Zero Trust initiatives. According to a Microsoft paper, Evolving Zero Trust, the best Zero Trust strategies are built on governance models designed to enforce data integrity through continuous monitoring and improvement.
In a 2021 McKinsey piece, analysts call security as code (SaC) the “best (and maybe only)” way to secure cloud apps and systems. These solutions allow users to implement security protections at speed and scale, setting system-wide rules that automatically enforce compliance, generate value, and mitigate risk.
The main advantage of SaC tools is, they offer more control over security and save IT teams a ton of time. For example, security policies may be translated into processes any time there’s a change made to the source code.
Automation is now a prerequisite for establishing a strong, sustainable security posture. Consider the sheer volume of security alerts and notifications alone and you can see why automation is the only way to ensure that your organization is always prepared to take immediate action in the face of a threat.
Security automation plays a key role in dealing with routine IT tasks such as provisioning, scripting, and performing access reviews – all without human intervention.
Leading orgs use security automation in more advanced ways. Think – using machine learning models to orchestrate adaptive defense strategies that take proactive action against threats.
Automation also enables businesses to quickly recover from an attack by allowing you to rapidly contain and remove malware from your environment – and rebuild once you get the green light to move forward.
Accenture experts say automation increases resilience capabilities on all fronts – prevention, detection, response, and recovery.
Analysts also note that many organizations don’t realize that other efforts to modernize infrastructure and processes extend naturally to cyber defense. Ultimately, though, business leaders need to shift their mindset and start embracing security automation as part of their overall resilience strategy.
As mentioned up top, Zero Trust doesn’t represent the full picture of your best possible ransomware strategy. Rather, it’s a template that can offer a strong foundation for a tailored, defense against evolving threats – if you can manage to get everything else right.
The challenge is, cybersecurity, like all digital strategies, demands a data-driven, one-of-a-kind approach. And, naturally, it can be hard to figure out what solutions you need and how to implement them – let alone how to establish strong governance models or leverage security automation capabilities.
To get started, we recommend checking out Microsoft’s Zero Trust Maturity Assessment. It’s a short series of self-guided quizzes that can help you understand your current security posture and point you in the right direction.
From there, you might reach out to a partner like Velosio that can work with you to develop and implement a game plan that not only protects against ransomware, but generates real value for your business and its customers. Contact us today to learn more about our services, solutions, and how we approach security.
Talk to us about how Velosio can help you realize business value faster with end-to-end solutions and cloud services.