Protecting On-Premises Microsoft Dynamics from Ransomware
Discover how to protect on-premises Microsoft Dynamics from ransomware, as you nail down the logistics of migrating to the cloud for real.
Table of Content
Despite what some legacy holdouts may still believe, on-premises systems aren’t more secure than their counterparts in the cloud.
On-prem tech is vulnerable to many of the same threats facing cloud-based apps and services — and then some. It’s now seen as a liability – posing a serious threat to customers, partners, and even your org’s chances at long-term survival.
Companies using legacy ERPs also face additional risks due to silos, blind spots, and a lack of real-time data syncing. That, in turn, means they can’t detect and respond to threats quickly enough to ensure a quick recovery – and avoid the devastation of a fast-moving attack.
Without proper protections in place, cloud-based ransomware can infect on-prem systems via phishing and credential theft, brute force and backdoor attacks, and other more sophisticated methods.
In this piece, we’ll explain how to protect on-premises Microsoft Dynamics (and other legacy tech) from on-premises ransomware, as you nail down the logistics of migrating to the cloud for real.
Okay, it’s rare for a company to operate without relying on any cloud-based tools.
Even if you’re still using an on-premises Microsoft Dynamics ERP, your company probably conducts some business in the cloud.
Consider the tools your teams use on the job. They’re definitely using email, and likely a handful of productivity apps like Microsoft Teams, Trello, or Google Workspace. Your sales team probably uses some sort of cloud CRM like D365 Sales or Salesforce. And, maybe there’s an HR person that uses a payroll integration that syncs payment data back to your core financials. You get the idea.
What that means is, your on-prem ERP is directly linked to the cloud – which means that data is now exposed to the same risks facing cloud storage solutions and web apps.
Cloud services are managed by a vendor, security is included in your subscription.
It’s rare that the average SaaS tool is the source of a serious breach or on-premises ransomware attack, given that it’s in your provider’s best interest to protect its users from data leaks, fraud, and malware – because, well, it’s bad for your business.
Still, breaches happen. Vulnerabilities always exist, and sometimes, threat actors exploit them before vendors have time to come up with a fix.
Look at the SolarWinds attack. Trojanized code was inserted into a file later distributed as part of an Orion software update. Thousands of customers downloaded the malware, and the company had no idea for several months – until one customer’s security system picked up on signs there had been a breach.
Keep in mind, malware infections spread in both directions. Compromised on-prem files can propagate cloud environments and infect apps and services containing customer data, communication logs, trade secrets, IP, etc.
Older, on-prem systems tend not to include security features that come standard with newer, cloud-based solutions like endpoint detection, antivirus protections, and adaptive threat intelligence.
Unfortunately, those poor protections make it easy for attackers to run the entire on-premises ransomware and data exfiltration attack chain from one system, with little effort. As you might imagine, finding these glaring vulnerabilities in the wild is a small victory for threat actors – a chance to make some easy money.
Though legacy ERPs and old school security solutions can be a huge liability, there’s a lot you can do to harden your security posture. Microsoft recommends starting with some general best practices, such as:
Beyond those basics, you’ll need to establish end-to-end coverage across the entire network – including all endpoints, identities, devices, machines, apps, databases, subscriptions, APIs, connectors, configurations – anything linked to your digital footprint.
If you’re not sure where to look, we recommend checking out the Zero Trust framework, which breaks coverage into individual “security pillars,” pictured in the screenshot below:
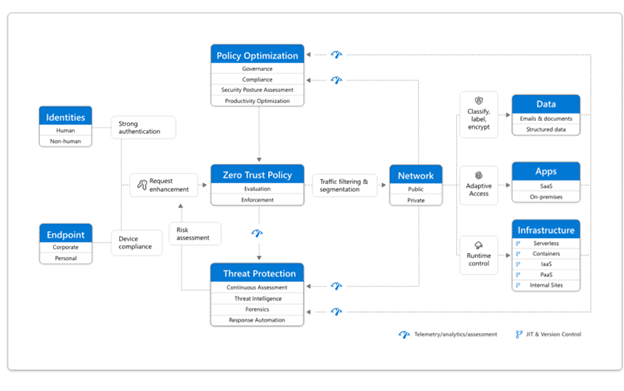
Data from Deloitte’s 2022 “Future of Cyber” survey revealed that end-to-end visibility across complex systems is key to balancing security requirements with digital transformation goals. Experts note that the stakes of getting this wrong include operational disruptions, reputational damage, diminished equity valuations, among other disasters.
The first step toward gaining control of your security posture is combining everything into one hybrid environment. That way you can manage and secure your entire ecosystem from a “single pane of glass.”
As an example, when butter giant Land O’Lakes sought to improve its security posture, the company needed a way to combine old and new solutions in a flexible hybrid workspace – without the friction and frustration of more fragmented solutions.
Land O’Lakes combined several solutions to simplify security operations across its complex landscape. Together, Microsoft Sentinel and Defender for Cloud provide a single source of truth for monitoring and securing the entire digital estate.
They also use Azure Kubernetes Service (AKS) to proactively manage massive datasets stored in secure containers, while Defender for Containers and Sentinel offer granular visibility into the company’s expansive container ecosystem and its workloads, spanning a diverse range of environments.
Defender for Cloud made it possible for the Land O’Lakes team to find and fix bad containers before deployment, while Azure DevOps allowed them to establish, automate, and enforce best practices preventing the kinds of minor errors that cause problems later on.
Senior Security Engineer Michael Marsh said the company immediately saw the “connectedness” of the Microsoft environment a major advantage over other solutions – noting it picked up signals other stacks may have missed.
You might also look toward something like Azure Arc, which is designed to unify disparate apps, tools, machines, and devices – online and off – in one cohesive hybrid ecosystem, making it easier to develop, manage, and secure all resources from one place.
Arc aggregates security data from all connected resources – whether that’s “ephemeral” Kubernetes clusters, Linux Servers, on-prem Microsoft Dynamics software, or the homegrown legacy apps still attached to your stack.
Within the Microsoft ecosystem, you’ll find several tools that enable real-time monitoring across your entire threat landscape.
Microsoft Sentinel offers continuous monitoring across all assets – with a core focus on intelligent detection and response.
Defender for Cloud protects hybrid environments and workloads – continuously scanning systems for vulnerabilities. Its built-in AI then serves up recommendations for fixing issues – and even suggesting security policies you can implement and enforce across all resources in a matter of clicks.
Defender for Endpoint, on the other hand, offers full detection coverage across the entire attack chain. discovering endpoints and devices connected to your network.
Azure Monitor is used mainly for optimizing asset performance – offering a unified solution for storing, monitoring, and managing the operational telemetry across your entire network – and the apps and infrastructure that support critical operations.
Users can capture data from both on-premises and cloud environments, set up alerts, and use ML-powered insights to identify problems and explore solutions.
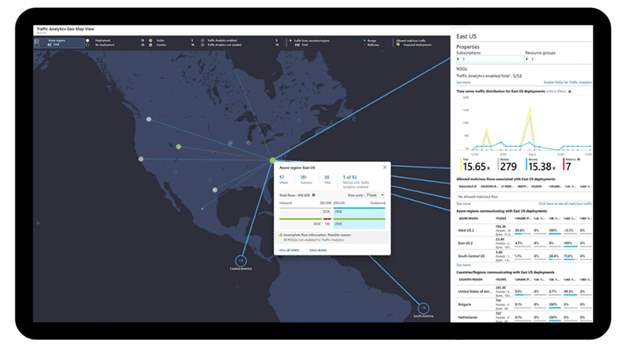
In the screenshot below, you can see Azure Monitor’s Map View, which allows users to monitor, diagnose, and resolve networking issues without logging into individual virtual machines (VMs). They can also trigger packet captures, analyze group flow logs, and establish tighter network controls based on the platform’s super granular performance insights.
As the Land O’Lakes case study made clear, Microsoft’s Security tools were made for layering.
Each security tool in Microsoft’s expansive stack captures different insights and applies them in different ways – protecting your digital estate from different angles – be it governance, DevOps, detection, discovery, or response.
Ultimately, the tools you end up with depends on your environment. For example, a company that leans heavily on IoT devices and legacy equipment will have different needs than a professional services firm mostly operating in the cloud but still using a handful of on-prem databases.
One of the advantages of using a cloud-based ERP like D365 is that updates happen automatically — minimizing the risk that unsupported legacy apps or one missed update will leave your entire organization vulnerable to an attack.
If you’re using an on-prem version of Dynamics, you’ll need to be extra vigilant when it comes to locking down their system, performing backups, and scheduling updates. Always install all security updates ASAP, as they fix known vulnerabilities.
You’ll also want to automate and streamline processes whenever possible. It’s way too easy to skip that routine update, fail to remove PII data per consumer privacy regulations, or overlook that one exposed endpoint that ends up taking down the whole system.
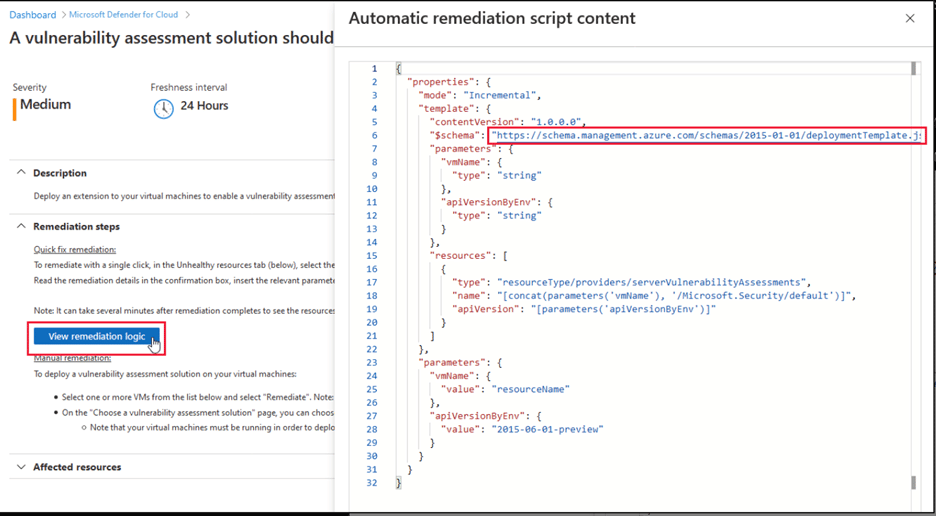
Microsoft offers several options for automating software updates, patches, and performing time-consuming, error-prone IT tasks. For example, Defender for Cloud, Endpoint, Servers, etc. come with a vulnerability assessment tool that allows users to turn recommended remediation steps into automation scripts.
Just because you’re not 100% in the cloud, doesn’t mean you’re safe from ransomware attacks.
Regardless of where you are in your journey to the cloud, ransomware represents an urgent threat that needs to be addressed before you do anything else.
That said, hybrid environments can be tricky – particularly when you’ve got a legacy ERP like Dynamics NAV or AX supporting all of your digital operations. Remember, these solutions were built on last generation’s infrastructure, and therefore, aren’t equipped to unlock the “transformative” potential that today’s solutions have to offer.
From a security standpoint, focusing on unity and coverage should be enough to keep you safe as you sort things out. But – you’ll need to move to a cloud ERP to unlock the full range of benefits a proactive, intelligent ransomware strategy can provide.
While Velosio isn’t a cybersecurity company, security is baked into everything we do — from cloud migrations and ERP implementations to digital transformations and ongoing support. We’ll help you evaluate your security posture, ID risks, and implement secure solutions whether you’re looking for temporary on-prem protections or you’re ready to level up with more advanced solutions.
To learn more about the services we provide and how security fits into the bigger picture, contact an expert today.
Talk to us about how Velosio can help you realize business value faster with end-to-end solutions and cloud services.