Building Security, Compliance, and Trust in the Microsoft Cloud
Learn how the Microsoft Cloud allows you to build a secure design by covering all your company's big security bases.
Table of Content
The Microsoft Cloud is a massive win for hybrid work. It allows you to build an integrated system that’s secure by design, covering all your major security bases in a single environment.
That means end-to-end visibility, holistic protections, and cutting-edge tech that can adapt and automate critical tasks while your team focuses on other things.
In this article, we’ll look at ways you can keep your organization safe by harnessing the power of the Microsoft ecosystem.
In the big picture, the Microsoft ecosystem allows hybrid organizations to build an integrated, adaptable cybersecurity strategy based on the principles outlined in the Zero Trust framework.
Real quick, let’s go over the security features built right into the core apps:
Windows 11 and Windows 365 provide a secure foundation for enabling hybrid work – allowing IT pros to manage and secure all MS 365 apps from one central hub.
Within Teams, SharePoint, OneDrive, Excel, Outlook, and the rest of the gang, you’ll find embedded security features including data encryption, DLP, sensitivity labels, MFA, SSO, and anti-malware filters.
Security settings for both Dynamics 365 and the Power Platform can also be configured and managed through the Microsoft 365 admin center — all of which are hosted within Azure’s datacenter.
In a July blog, Microsoft explained that moving all employees and workloads into the cloud was only made possible by adopting a Zero Trust strategy.
MS employees have long had remote access to some apps and responses via VPN. But, with more work shifting away from the office and into the cloud and a threat landscape growing more complex by the day, Microsoft’s perimeter-based approach had become a liability.
Zero Trust is a security framework that operates on the core principle: “never trust, always verify.”
So, if you’re using Zero Trust, every app that an employee uses automatically enforces its own protections (and, yes, that’s every time they try to log in). Users can’t get into an app until it can confirm the device hasn’t been compromised.
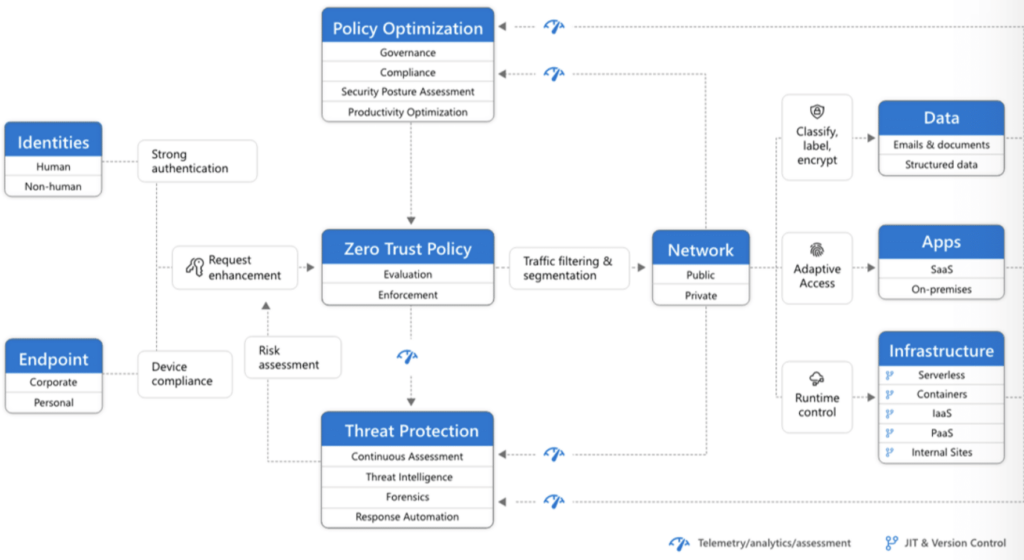
The MS ecosystem helps IT leaders safeguard critical assets and get ahead of potential threats — without encroaching on hybrid workflows – with end-to-end visibility, layered protections, and granular controls.
“People finally get to move away from that traditional experience of being locked behind a firewall. When all your apps are connected in the cloud and protected with baked-in security controls, people can get all their data directly from Teams or integrated tools like Excel, PowerPoint, or Power BI. And, that’s just huge.” says Velosio IT Director Eric Robertson.
In a hybrid work environment, employees may be working from various locations, using different devices, networks, and applications. This expanded attack surface provides more opportunities for cybercriminals to exploit vulnerabilities and gain unauthorized access to sensitive data.
“Lately, we’ve been having a lot of conversations with clients who are struggling to understand how they can wrap their arms around their workforce and all the devices and apps touching critical data and assets,” says Carolyn Norton, Velosio’s Director of Cloud.
From a security standpoint, you need to understand that there’s data out there that’s important to the organization. Whether that data is mission-critical or not, you need to be able to see what’s going on inside your network so you can protect yourself.
To overcome this challenge, hybrid leaders need to focus first on establishing network-wide visibility.
“Just bringing everything together in one place makes a huge difference. But, when they start talking to each other, you’ll get way more signals,” says Eric.
“So, you can then look at your dashboard and immediately think, ‘hey, this doesn’t make sense. Why are we seeing X or Y here when Z device is all the way over there? After a while, you can kind of connect the dots and identify things faster in order to remediate,” he says.
You can analyze security insights against workforce analytics, employee feedback, financial reports, and so on to make smarter decisions about supporting hybrid teams. And – ensure you always do this in a way that protects critical assets and data.
Before you make any changes, you’ll need to get a baseline for how existing solutions are performing. You might start by checking your MS 365 Secure Score in the Microsoft 365 Defender portal.
This built-in assessment flags vulnerabilities and improvement ops that you can use as a jumping off point for building out the rest of your strategy.
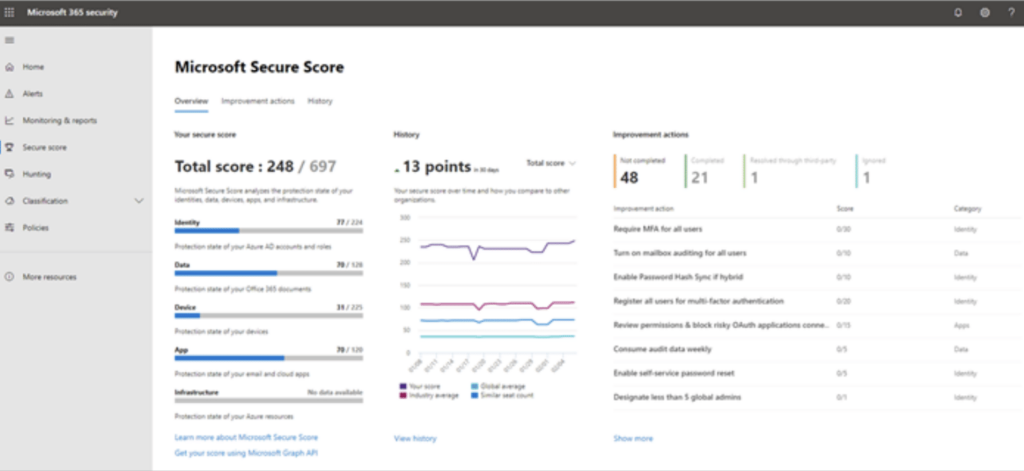
Microsoft put together a list of 12 security tasks for securing hybrid environments. While this doesn’t cover the full scope of implementing Zero Trust, it does put you on the right path.
Multi-factor authentication (MFA) prevents unauthorized access by requiring users to provide additional verification like a fingerprint or a code sent to a trusted device, in addition to their password.
You can use Entra ID (formerly Azure Active Directory) to set up MFA, then start working toward a more comprehensive conditional access strategy that uses identity and access signals to detect, investigate, and remediate risks.
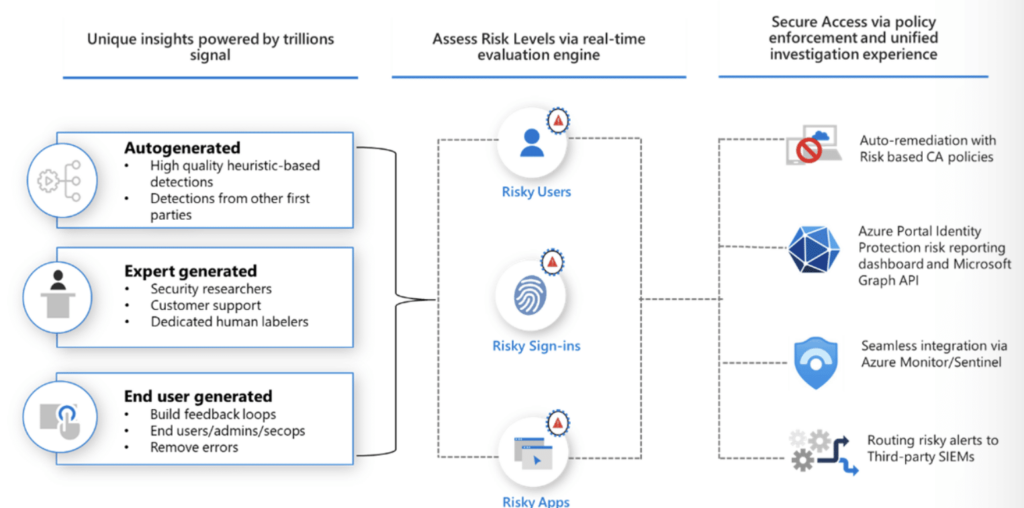
All Microsoft 365 plans come with several features that protect your business from threats – and you’ll configure these either in your Office 365 admin center or the Defender for 365 portal.
Make sure that audit logging is enable across all apps in your network. It should be “on” by default, but sometimes settings get changed in the midst of a major implementation. Once that’s confirmed, start securing your Office by focusing on these four areas:
Malware – In the Defender Portal, you can configure protections on the Anti-Malware page by selecting “Edit Protection Settings” from the Protection Settings menu.
Then: Turn on the common attachment filter, then choose “select file types” to add any file types not included by default. When the system locates the file types you selected, confirm that you’d like to reject the message with a non-delivery report.
From there, you’ll want to enable Zero-Hour Auto Purge (ZAP) for malware. Then, you’ll set up a quarantine policy to define rules such as what end-users are allowed to do with quarantined messages or whether they’ll receive alerts when a message is quarantined.
If you’re using a subscription with Exchange Online Protection (EOP), you can find instructions for configuring anti-malware protections here.
Phishing – Anti-phishing protection is included in Defender for Office, as well as any subscription that comes with EOP. You can also set up ZAP for Phishing and enable mailbox intelligence, impersonation protection, spoof intelligence, quarantine policies, and more.
Spam – Next, you’re going to enable anti-spam protections – define your policies, set up ZAP for Spam, and decide how you want to handle quarantines.
Malicious links & files – Defender for Office 365 allows you to enable time of click protections from malicious URLs and attachments in Teams, SharePoint, and OneDrive. You’ll want to enable Safe Attachments.
Defender for Office 365 integrates with your Office subscription to protect against threats lurking in your inbox and productivity apps (think – malicious links or attachments).
Next up, you’ll want to get set up with MS Defender for Identity. This cloud-based solution leverages on-prem Active Directory signals to ID, detect, and investigate threats.
Defender for Identity also uses end-user profile analytics, security reports, and other signals from across your network, then makes suggestions for how to improve your security posture.
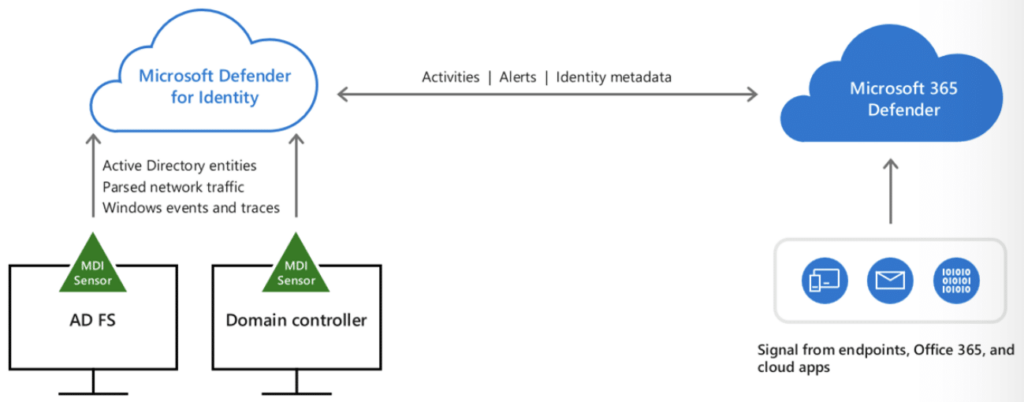
Defender for Microsoft 365 is an integrated defense suite that coordinates prevention, detection, and response activities across all identities, endpoints, and apps.
There are several different Microsoft Defender products – each designed to protect a different part of the threat surface:
Defender tools work together, sharing signals across the network and mounting a coordinated response to incoming threats using automated actions. In this example, you can see how Defender’s unified approach makes it easier for security pros to investigate an incident:
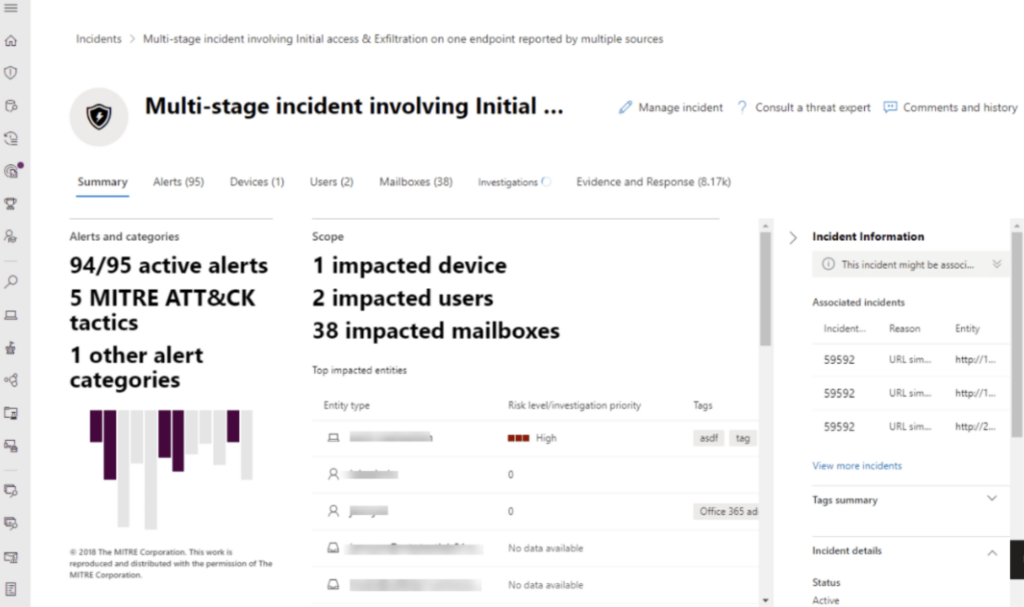
Rather than checking separate tools for endpoints, identities, Microsoft 365 apps, combining the data, and then analyzing it, everything is right there. That way, they can take action before malware spreads through the network.
Microsoft Intune Mobile App Management (MAM, for short) allows you to manage and protect business data on end user devices at the app-level.
Users can create App Protection Policies (APPs) for both Android and iOS devices that define which apps on specific devices are managed by the organization, as well as what users are allowed to do within each app (i.e.: can they download files, edit docs, access data, etc.?).
You can enforce these protections by creating conditional access rules in Azure AD that require data protections for all apps.
External collaborators don’t generally need access to your entire system. In these instances, it makes more sense to consolidate resources in OneDrive or Power Pages to prevent outside users from accessing your network.
Teams enforces security protections such as SSO, MFA, and data encryption across all Microsoft 365 apps, allowing you to configure external access permissions for specific channels. Within each channel, you can define what data they can view, modify, and share, what resources they can access, and so on.
For short-term engagements, you can grant temporary guest access that expires on a specific date. Say, when a project is finished or a contract ends.
Rather than focusing on perimeter-based protection, you’ll want to target the devices employees use to connect to the apps in your network. Now, there are different ways you can enroll employee/company devices (depending on the type of device and who owns it):
Once you’ve enrolled your devices, you’ll then need to configure app protection and device compliance policies.
Note that conditional access policies should reflect the needs of end users and workloads.
“As an example, if employees are working from home, there might be a scenario where people are allowed to use their own devices. But you might also have a different set of rules for company-issued devices vs. BYOD. Internally, we’re seeing more clients set rules that say, ‘yes, you can do X with your own device, but you need to do Y or Z with the company device and follow this procedure,” says Director of Cloud Carolyn Norton.
She adds that this approach gives remote teams more freedom, but at the same time, IT leaders need to think about setting policies that automatically protect data, operations, and end-users.
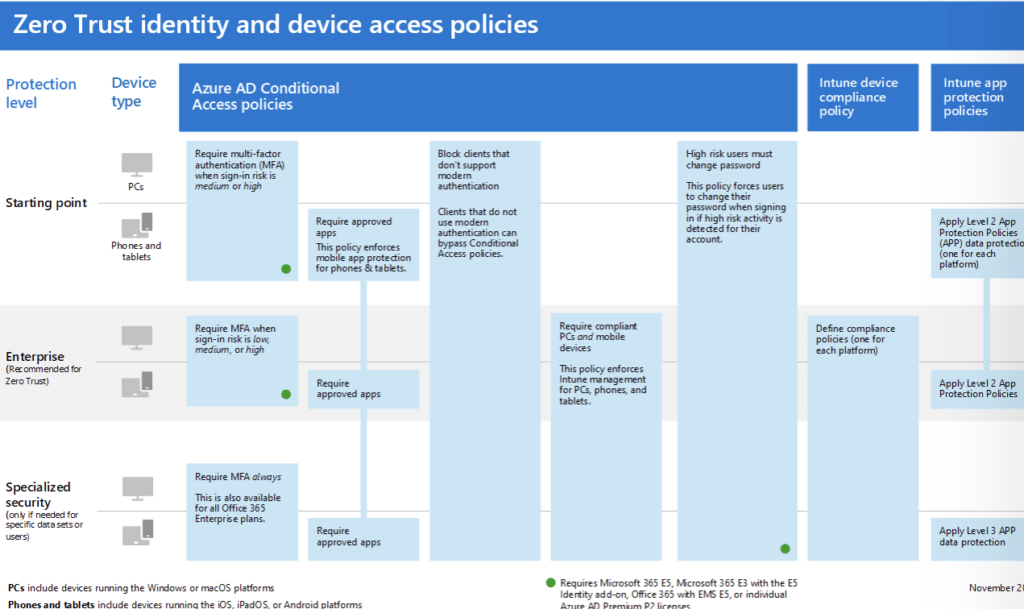
Microsoft Purview can help you implement these policies. Inside, you’ll find several tools that simplify compliance – regulatory assessments, compliance scoring, common control mapping, and more.
For example, Global bank, BTG Pactual used Purview’s Data Lifecycle Management, eDiscovery, and Compliance Portal to manage compliance across the entire infrastructure. Secure data connectors in Microsoft 365 helped the bank enable more secure, compliant use of core productivity apps.
When you shift to a hybrid model, that change in connectivity patterns can wreak havoc on your infrastructure.
You’ll need to make sure that your system is prepared to handle a sudden influx of activity from folks working from home. Otherwise, you’re looking at major performance issues that defeat the purpose of working remotely.
Hybrid environments often suffer from lax attitudes about cyber hygiene and security best practices. With the right tools in place, you can prevent a lot of these “human-driven risks.” But – you’ll still need to educate your teams re: cybersecurity threats and best practices.
Here are a few things to focus on:
Some resources you might use to bring your team up to speed:
Defender for Cloud Apps protects multi-cloud and hybrid environments threats and helps users proactively reduce risks across the entire cloud application lifecycle. It’s designed to provide full visibility into your cloud environment – but you’ll need to enable the App Governance feature first.
The platform identifies all cloud services in your stack and each service a risk ranking based on 90 risk indicators – plus remediation tips you can use to improve your posture.
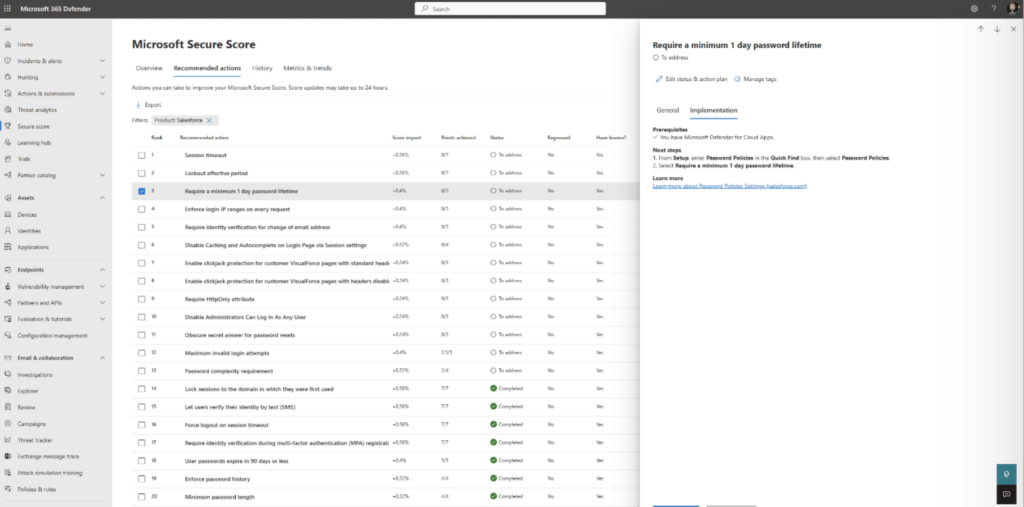
You can then use those insights to assess security and compliance across the network and set automated policies to monitor threat signals 24/7.
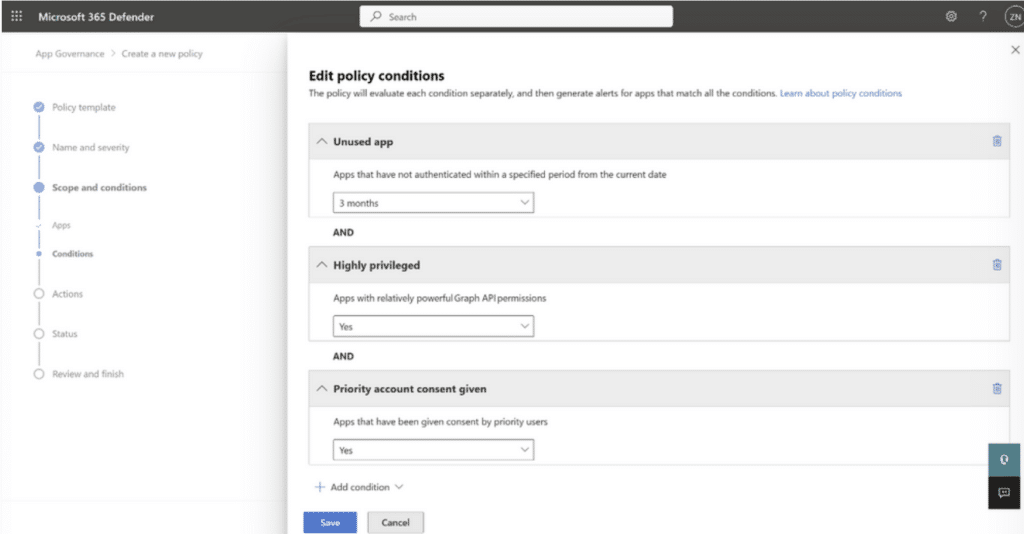
Defender for Cloud also includes a number of tools for protecting critical data using DLP features like sensitivity labels, removing external collaborators from confidential files, and blocking downloads to unmanaged devices.
Finally, you’ll want to create an SOC with integrated threat protection.
Broadly speaking, you’ll need to make sure your ecosystem has the following capabilities:
Microsoft Defender covers a lot of ground on this front. However, Microsoft offers several end-to-end solutions that can protect different types of data and assets across a range of environments, industries, and regulatory landscapes.
For example, Microsoft Sentinel detects threats using security analytics and MS threat intelligence. Sentinel uses AI to investigate threats and suspicious activity at-scale. It can also automate both basic security tasks and incident response.
You can learn more about implementing a security operations center here.
The tools within the Microsoft ecosystem can be combined and customized in a variety of ways to protect your system from all sides.
But, it’s important to understand that, like all hybrid strategies, you’ll need to approach security with a focused, objective-driven approach in order to reap the benefits these technologies can provide.
As with all hybrid strategies, you’ll need to approach security with a focused, objective-driven approach in order to reap the benefits these technologies can provide.
Establishing a Microsoft ecosystem allows hybrid organizations to build an integrated, adaptable cybersecurity strategy. Contact us now to learn how to empower your modern workforce with the Microsoft ecosystem.
Talk to us about how Velosio can help you realize business value faster with end-to-end solutions and cloud services.